How Phones and Amateur Radio Chose Different Paths
You receive a phone call from an unknown number. The voice on the other end claims to be your friend.
How do you know it's really your friend?
Perhaps you can go off of their voice. Does it sound like them?
Or you can ask them questions that only they would know the answer to. Maybe something like, "What's your favorite color?"
...except you realize in your five years of knowing them, you've never asked them for their favorite color.
Well, no worries! You start quizzing them on other trivia from your shared history, like their Netflix password or their childhood dream job and the first proud purchase they made with money from their actual job.
You realize, this is an interesting exercise in the difference between their public and private selves: what do you know about their private selves that a public impersonator wouldn't know?
This question of "how do we know who we're really talking to?" turns out to be one of the defining challenges of modern communication. Today, we'll explore how two sibling technologies, telephones and amateur radio, answered this question in completely different ways.
Divergence of Two Sibling Communities
For a long time, telephones and amateur radio lived in parallel universes. The similarities aren't hard to see: both relied on voice communication, both emerged from the same electromagnetic breakthroughs of the late 19th century, and both shared the same talent pool of people excited about electromagnetic communication.
Most importantly, both communities trusted nothing more than the sound of your voice and a simple identifier. In the telephone world, this identifier was a phone number. In the amateur radio world, this was your call sign.
If you sounded like yourself, that was enough.
But, while amateur radio stayed rooted in this community-trust model, phone networks had to scale to billions of strangers. At that scale, human trust wasn't enough. The phone networks had to learn math.
Phone Networks, and the Evolution Towards Zero Trust
In the early days of pre-digital, pre-cellular, phone networks were run much like the amateur radio world. If you had a phone plugged into the line, you were trusted. Billing was handled manually by operators or electromechanical systems.
Like amateur radio operators who trusted each other based on familiar voices and call signs, telephone users were part of a relatively small, interconnected community where social reputation mattered more than technical security.
However, in this simple and uncomplicated world of social trust, fraud was rampant. Phone phreaks used whistles and tones, often nothing more than the 2600 Hz whistle you find in a Captain Crunch cereal box, to trick the system into free long-distance calls.
But why did phone networks care so much about stopping fraud when amateur radio operators seemed content with their honor system? The answer lies in a fundamental difference between the two systems.
The important thing to note is that telephony was (and is) a commercial service. Every call generates revenue, and fraud in the form of free calls directly costs the companies money. This creates strong incentives to harden the system.
Now, in amateur radio, making a long-distance call doesn't cost anyone money. The FCC licenses operators to transmit, but they aren't paying per transmission. Therefore, there's no economic incentive for "phreaking" or gaming the system in the same way. Breaking the rules might get you a slap on the wrist or your license revoked, but it doesn't steal revenue.
Question: This begs the question, why didn't the phone phreaks just use ham radio to make long-distance calls? It's a free and legal alternative to phreaking.
Well, with ham radio, the person you want to reach must also have a ham radio setup! Not just that, but they must be tuned to the same band and available to reach you.
When you transmit to your friend's radio, it doesn't "ring" the same way a phone does. If they're not around to listen, they'll miss your transmission. You must tell them what time of day and which frequency band to listen to, and if the propagation conditions suck (read: bad weather), you must coordinate it all over again.
Imagine you're calling your Grandma in New York. Would you put her through all that trouble for a free transmission? It's really easier on you both if you call her by phone.
(Or, you know, get to phone phreaking with the small price of a Captain Crunch whistle...)
The phone companies clearly needed to adapt. They couldn't retreat to amateur radio's model, but they also couldn't ignore the growing economic damage from fraud. The solution would require rethinking the entire architecture of trust in telecommunications.
1G: Rise of the Castle-and-Moat Model
Let's introduce a trust model that will persist in future topics: the castle-and-moat model.
1G marked the first honest attempt at the castle-and-moat model. With 1G in the 1980s, we moved from the pre-cellular to cellular. Instead of wired telephones that were constrained to a single building like your home, we had phones that were mobile over large areas, that you could carry into your car.
Now that we let the phones out of the building, a new question emerged: how do we make sure that your phone is yours, and my phone is mine? And when you call me, how do I know that it's you?
To address this problem, phones identified themselves with an electronic serial number (ESN) and a subscriber number (MIN). The network trusted the phone if it provided the right numbers.
This ESN/MIN system was an early implementation of the castle-and-moat model: there's a castle that represents the internal, trusted network, and a moat that protects this castle. Untrusted outsiders must authenticate themselves with this moat to get into the castle.
A little hiccup with this solution was that criminals could easily copy your ESN/MIN and make calls, but it was a start.
2G, 3G, 4G: Castle-and-Moat, With Cryptographical Goodness
Clearly, asserting an identity wasn't enough. Phones needed to prove their identity.
The solution came with 2G's shift from analog to digital, which opened the door to something analog systems could never do: real cryptography.
What did cryptography look like in our analog 1G system? In an analog system, voice is transmitted as a continuous electrical waveform like this:
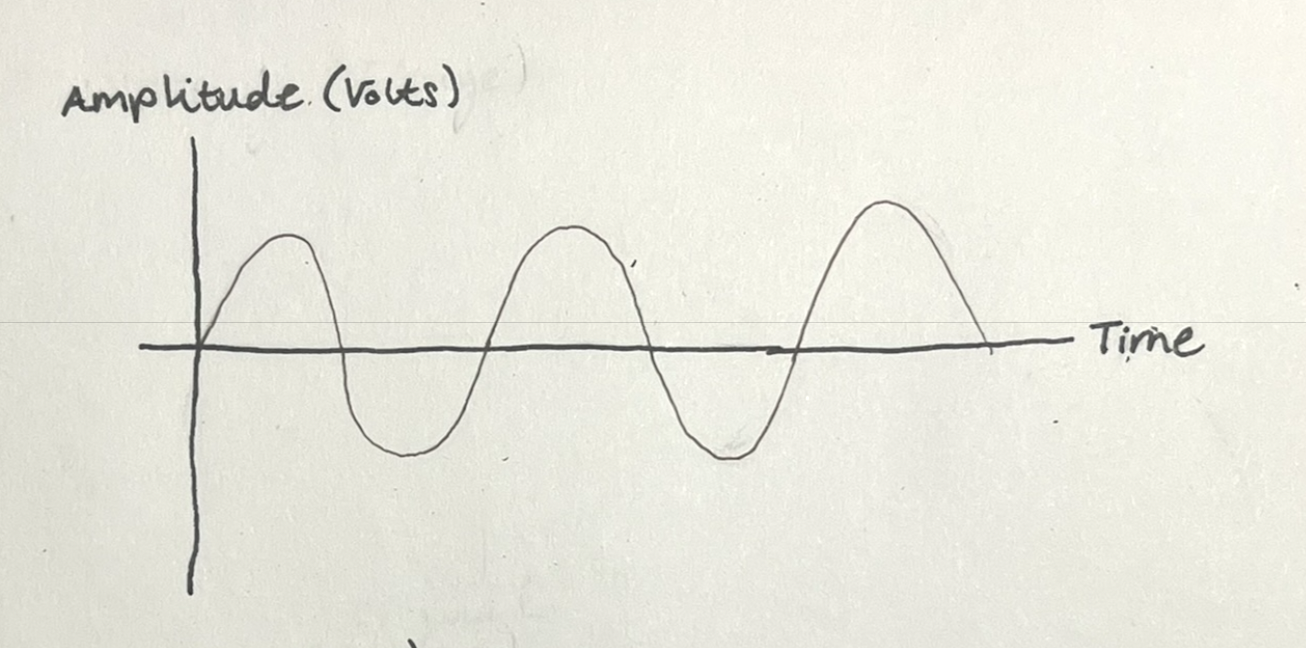
Encryption, in the mathematical sense, requires manipulating discrete data like bits using algorithms and keys. If we were to attempt some form of encryption with analog signals, we could only do crude scrambling like frequency inversion, which is not cryptographically secure.
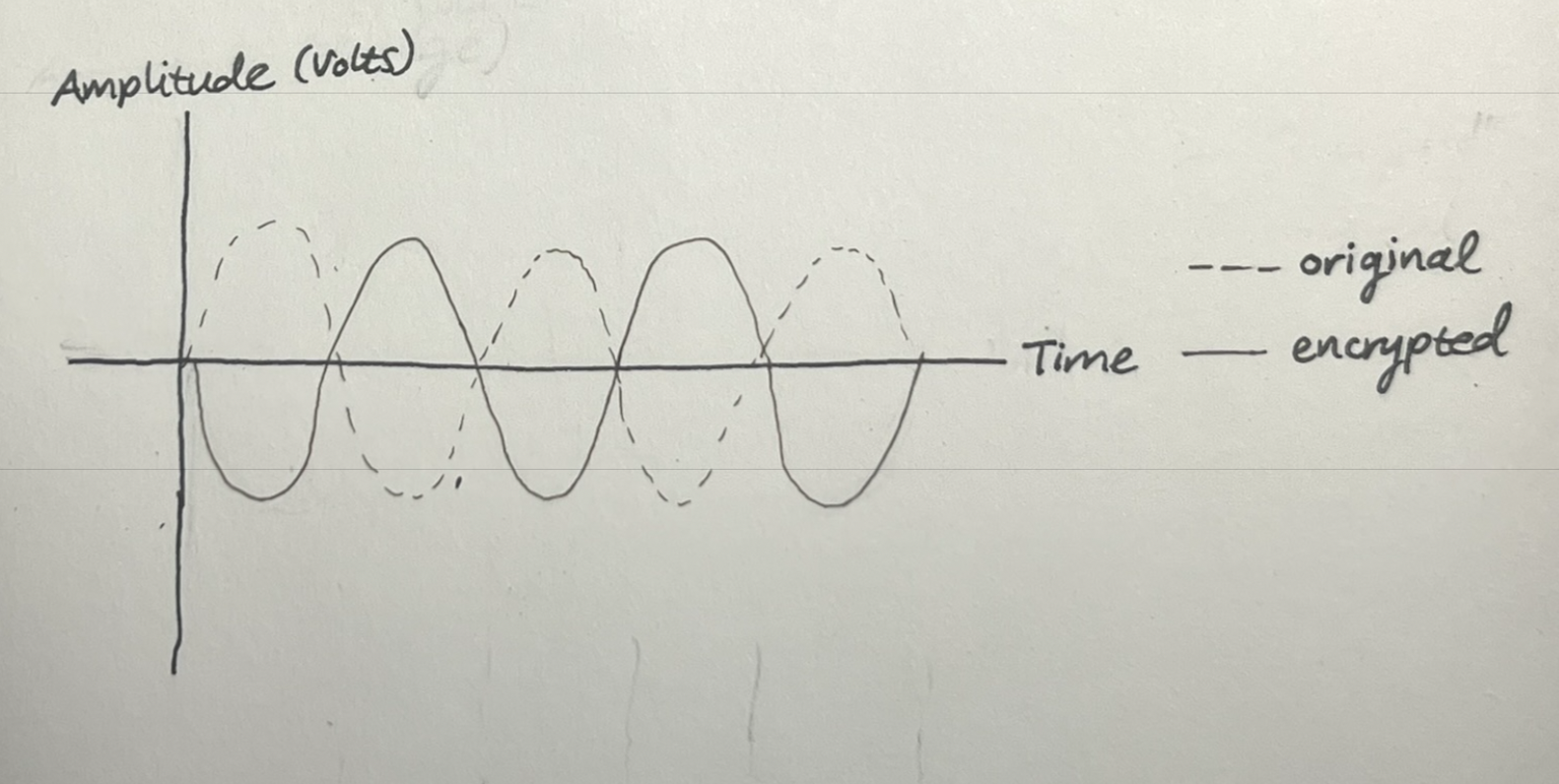
Frequency inversion scrambling, pictured above, was used in WWII systems like the Bell Labs A-3 scrambler, but easily defeated by applying the same inversion process... or even by trained listeners who could understand nearly half the words. It was not cryptographically secure by any means!
So, 2G introduced digital encoding, where voice is converted into a stream of 0s and 1s. Now each piece of information is represented as bits, which can be fed into cryptographic algorithms, and from here, we let the math do its thing and provide us with wonderful cryptographic security.
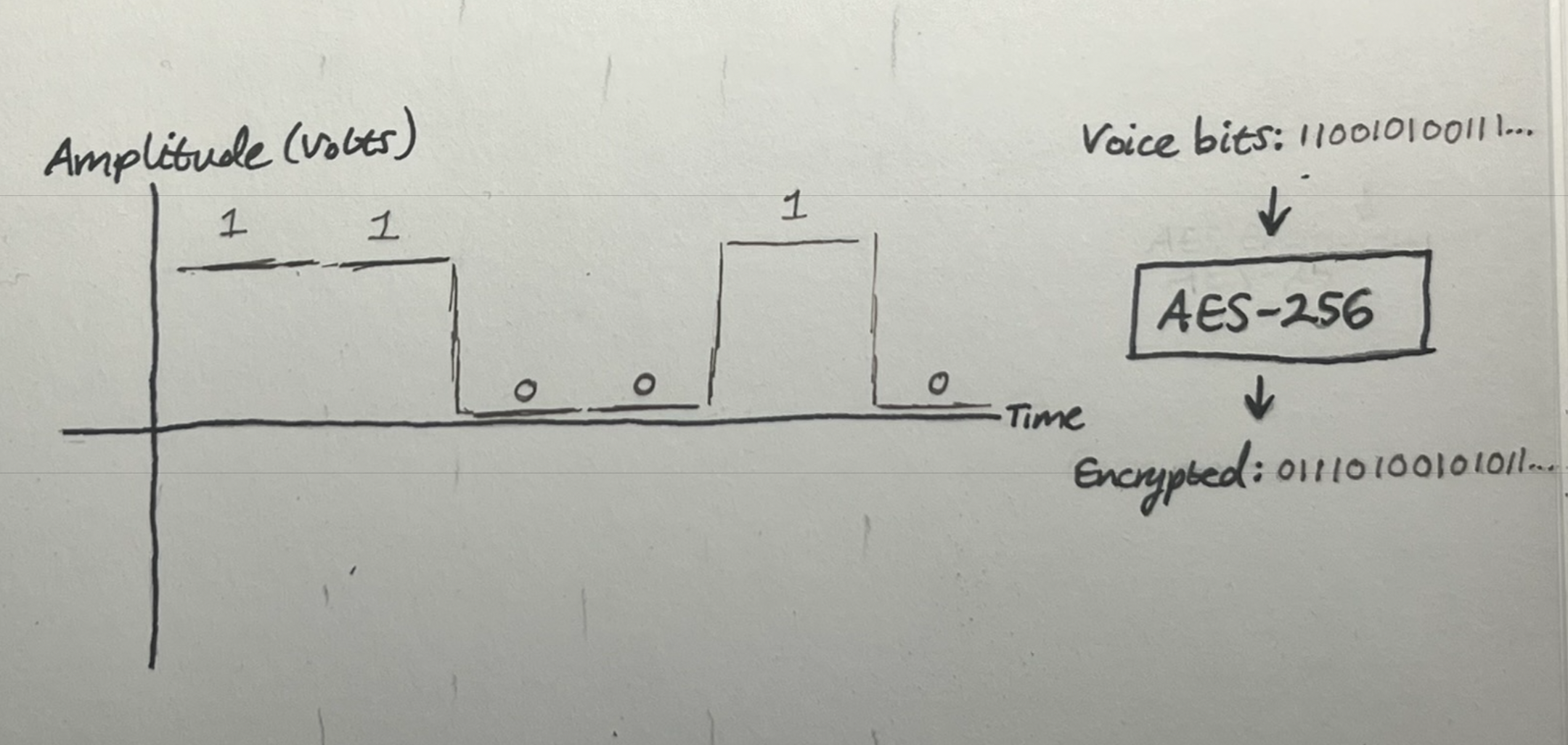
Discrete bits can be processed by mathematical encryption algorithms like AES, producing cryptographically secure output.
To implement their cryptographic system, 2G introduced a small but mighty addition to your phone: the SIM card, in charge of storing a secret key (Ki). When your phone speaks to a cell tower, the tower sends your phone a random number, the SIM card in your phone computes a response using its secret key, and the network verifies this response.
This was a huge leap in the history of phone networks. Phones no longer just asserted an identity; they provided it cryptographically.
In short, the transition to digital enabled new mechanisms in authentication and error detection that further generations like 3G and 4G iterated upon.
5G: The Move Towards Zero Trust
Each generation built stronger walls around the castle, but attackers kept finding new ways over the moat. By the time 5G arrived, network designers realized they needed a fundamentally different approach: what if there was no castle at all?
Today, as of writing in 2025, we are moving towards a zero trust model with 5G.
You can think of the zero trust model as deleting the castle from the castle-and-moat model.
In the castle-and-moat model, you authenticate yourself, you enter the castle, and you don't have to authenticate yourself again until you leave the castle.
In the zero-trust model, there's no longer this idea of a castle with trusted insiders and untrusted outsiders. Everybody is untrusted by default. You authenticate yourself every time you take an action that requires trust.
5G implements zero-trust principles through several key innovations. For one, mutual authentication is now mandatory, meaning both your phone and the network must prove their identities to each other, rather than just the phone proving itself to the tower.
Additionally, there's this idea of virtual "slices." The network creates "slices" for different applications, each with its own security rules; an enterprise slice might continuously verify every device, user, and app throughout a session rather than trusting them after initial login.
Perhaps most importantly, 5G enables end-to-end encryption that protects your data from your device all the way to the service you're using, not just between your phone and the nearest cell tower. This means even if someone compromises part of the network infrastructure, your communications remain protected by multiple layers of continuously-verified security.
Amateur Radio: The Road Not Taken
Phone networks, amateur radio.
Remember, these two communities started from exactly the same place. Both communities trusted nothing more than the sound of your voice and a simple identifier.
If you sounded like yourself, that was enough.
While phone networks raced toward zero trust with their Byzantine protocols and continuous verification, amateur radio operators still live in that simpler world where your voice and call sign remain sufficient proof of identity.
If you sounded like yourself, that was enough. And remarkably, it still is.
Amateur radio evolved, yes, and began experimenting with digital voice and data, but its ethos of transparency remained largely unchanged. The FCC explicitly bans encryption in interest of transparency, a policy that has persisted to this day.
You can see for yourself. Open up APRS.fi, and you'll see the live positions of hobbyists from all over the world, from cars, balloons, and hiking trips. You, too, can broadcast your position to the open airwaves, and let your next expedition be seen by the rest of the community.
Should you get your hands on a scanner app or an SDR dongle for an affordable price of ~$30, you can tune in to local ham bands and hear chatter. Again, no encryption, nothing hidden. (Try listening in on a phone call that way. You can't, since phone networks encrypt everything by design!)
Aside from being a wonderful way of sharing little status updates and shooting the breeze with a close-knit community, amateur radio can be used for social good. During natural disasters when cell towers fail and internet connections go dark, amateur radio operators often provide the only reliable communication links for emergency services. Hurricane Katrina, the 2010 Haiti earthquake, and countless other disasters have demonstrated how this technology becomes invaluable when modern infrastructure fails.
A Pattern Emerges
The history of phones and amateur radios show that trust models can evolve very differently by scale. The phone network, with its need to scale to billions of users, needed to evolve from pure social trust to a castle-and-moat model. In response to attackers, this castle-and-model was hardened with cryptographic protocols, and with 5G, we see phone networks moving towards a zero-trust model.
The amateur radio world, however, remains a small, tight-knit community that continues to rely on social trust.
This evolution from community trust to castle-and-moat to zero trust isn't unique to phones. Your home WiFi network faces the same scaling pressures that forced 1G to become 5G. Your web browser navigates the same tension between openness and security that split phones and amateur radio down different paths. Even your PC games are wrestling with questions of trust that would be familiar to a 1960s phone phreak.
There's a lot of ground to cover, and we'll explore those other parallels in the upcoming chapters. It'll be exciting, for sure.

